 Steganography Wing
Steganography Wing Steganography Wing
Steganography Wing
It is not the study of stegosauruses. It doesn't even have the
same root ("stega" vs. "stego"), although as reader Peter Ecker was
kind enough to point out, stega ("covered") and stego
("roof") are semantically related. Please forgive the pun.
| Exhibit | Description | |
|
png file with concealed version of css-auth.tar.gz |  The judges in the Great
International DVD Source Code Distribution Contest decided to give
the award for best high-tech hack value to Andrea Gnesutta, whose entry
was the little banner image above. To extract css-auth.tar.gz from
the graphic file, dvd_scdc_tst.png, go to byte 0x002428 and copy the
next 0x547E bytes to another file.) The judges in the Great
International DVD Source Code Distribution Contest decided to give
the award for best high-tech hack value to Andrea Gnesutta, whose entry
was the little banner image above. To extract css-auth.tar.gz from
the graphic file, dvd_scdc_tst.png, go to byte 0x002428 and copy the
next 0x547E bytes to another file.)
| |
|
jpeg file with concealed version of css-auth.tar.gz |
 Inspired by
Andrea Gnesutta's idea, this is a JPEG image file with the source code
concealed inside it. This file should be viewable in all browsers. Inspired by
Andrea Gnesutta's idea, this is a JPEG image file with the source code
concealed inside it. This file should be viewable in all browsers.
| |
| gif/zip file
with css_descramble.c | ||
|
"Not the DeCSS Source" |
| |
|
Prime number encodings: Carmody Hannum 8-bit Hannum 7-bit Jobling Carmody's executable prime | Inspired by Phil's effort, two prime number encodings of the source of efdtt.c (not gzipped) have been contributed by Charles M. Hannum, and a prime number encoding of a variant of qrpff.pl has been developed by Paul Jobling. Phil Carmody subsequently created the first non-trivial executable prime, an implementation of Hannum's efdtt.c for the Intel architecture. For more information, see Tom Greene's article in The Register. Here's the official Prime Curios entry. | |
| Jack Valenti brings you efdtt.c |  Here is the source of efdtt.c, the
434 character C decryption program, embedded in a photograph of MPAA
president Jack Valenti. The embedding was done with Xerox DataGlyphs technology. You can
read more about DataGlyphs in this article from the March
2001 issue of IEEE Computer. Contributed by Tim Scott. Here is the source of efdtt.c, the
434 character C decryption program, embedded in a photograph of MPAA
president Jack Valenti. The embedding was done with Xerox DataGlyphs technology. You can
read more about DataGlyphs in this article from the March
2001 issue of IEEE Computer. Contributed by Tim Scott. | |
| X-Face header is efdtt |
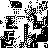 Benot Rouits writes:
"X-Faces are ASCII icons intended to show in low-quality the face
of an e-mail author... Most Unix mailreaders and Mac ones handle
X-face headers... *Anyway*, the purpose of this thumbnail was for me a
mean to express a kind of personification of efdtt.c since it can be
now seen as a *face*... More informaton about X-Face header can be
found here: http://www.dairiki.org/xface." Benot Rouits writes:
"X-Faces are ASCII icons intended to show in low-quality the face
of an e-mail author... Most Unix mailreaders and Mac ones handle
X-face headers... *Anyway*, the purpose of this thumbnail was for me a
mean to express a kind of personification of efdtt.c since it can be
now seen as a *face*... More informaton about X-Face header can be
found here: http://www.dairiki.org/xface."
| |
| get CSS-auth from a DNS server | This is a Unix shell script (/bin/sh) containing the following sequence of commands: for DVDs in Linux screw the MPAA and ; do dig $DVDs.z.zoy.org ; done | perl -ne 's/\.//g; print pack("H224",$1) if(/^x([^z]*)/)' | gunzip. Explanation: a hex dump of the gzipped css-auth code was used to generate a bunch of host names in a DNS server. (DNS, or Domain Name Service, is how host names get mapped to IP addresses.) The dig command is used to query the server and extract the entries; the rest of the commands reformat the output to recover the C source code. This code comes from Samuel Hocevar's 42 Ways to Distribute DeCSS. | |
| DNA sequence |  css_descramble.c as a 43,016 base pair DNA sequence, contributed by Joerg Dietrich, who says:
"Maybe somebody with a local copy of the Human Genome Project database
on his personal supercomputer can find this sequence in our genetical
information. This would mean nearly 6 billion lawbreakers on this
planet." The encoding is a simple substitution cipher, produced by this Perl code. css_descramble.c as a 43,016 base pair DNA sequence, contributed by Joerg Dietrich, who says:
"Maybe somebody with a local copy of the Human Genome Project database
on his personal supercomputer can find this sequence in our genetical
information. This would mean nearly 6 billion lawbreakers on this
planet." The encoding is a simple substitution cipher, produced by this Perl code. | |
| Minesweeper Game | ||
| css_descramble.c encoded in the DMCA | Here is css_descramble.c encoded as a collection of seemingly random lines drawn from the text of the Digital Millenium Copyright Act. It was contributed by Sham Gardner. Each byte of the original source has been used as an index into an array of unique, non-blank text lines. Basically, it's a one-to-many substitution cipher. You can read more about this encoding technique and download the Perl code from Sham's page. | |
| Zero-click DeCSS | Here's a page of search engine queries courtesy of Cameron Miller. Click on any link to search for DeCSS. So the page is really a list of links to lists of links. But wait -- are you really two mouse clicks away from having the DeCSS "virus" infect your computer? What's that thing in the page's META tag? (Select "View Source" in your browser to see the META tag.) Whoops! There it is! | |
| Trojan Cow |  Trojan Cow is a scheme for
distributing the DeCSS source by embedding it in image files that
become part of official government document collections, such as the
set of comments submitted to the Librarian of Congress concerning the
DMCA. There are actually two cows involved, and the technique for
recovering the code is a secret (hence, presumably protected by the
DMCA.) Contributed by Karl O. Pinc. Trojan Cow is a scheme for
distributing the DeCSS source by embedding it in image files that
become part of official government document collections, such as the
set of comments submitted to the Librarian of Congress concerning the
DMCA. There are actually two cows involved, and the technique for
recovering the code is a secret (hence, presumably protected by the
DMCA.) Contributed by Karl O. Pinc.
| |
| Whitespace encoding |
Rene S. Hollan contributed this example of self-documenting steganography: the source of css-descramble.c is encoded in the patterns of spaces between words, while the words themselves explain the encoding! Sample text: "Consider a file format where data modulates non-leading and non-trailing spaces between non-space tokens of a plain text file...." The C++ source for the encoding and decoding programs is included in this gzipped tar file. | |
| Zapf DingCSS and | 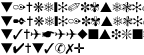 Zapf Dingbats encoding of the DeCSS source (in a PDF
file). A simple substitution cipher, contributed by Faisal Jawdat of faisal.com. Zapf Dingbats encoding of the DeCSS source (in a PDF
file). A simple substitution cipher, contributed by Faisal Jawdat of faisal.com.The ROT13 encoding submitted by Travis Kroh is also a substitution cipher, but one where the encoding and decoding algorithm are the same. | |
| ASCII art | 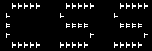 This ASCII art
encoding of the css_descramble.c source file contains nothing but
pound signs (#), spaces, and carriage returns. It's another example
of human-readable source code that is not readable by a C compiler.
Contributed by Nicolas
Ribot. This ASCII art
encoding of the css_descramble.c source file contains nothing but
pound signs (#), spaces, and carriage returns. It's another example
of human-readable source code that is not readable by a C compiler.
Contributed by Nicolas
Ribot. | |
| Typo encoding |
Here is a typo-laden transcript of day 6 of the New York DVD trial. We're talking a lot of typos here. In fact, there seems to be a typo about every 17 characters. The typos encode the text of css_descramble.c. The encoding/decoding program can be found here, and the uncorrupted source for the transcript here. (Contributed by Scott A. Crosby.) | |
| GNUPG'ed source |
 -----BEGIN PGP MESSAGE----- An encrypted copy of css_descramble.c,
produced by GNU Privacy Guard (GPG).
To decrypt it, you need to know that the secret pass phrase is
"speechiscode". Under what circumstances would the encrypted file be legal to publish?
(Contributed by Scott A. Crosby.)
-----BEGIN PGP MESSAGE----- An encrypted copy of css_descramble.c,
produced by GNU Privacy Guard (GPG).
To decrypt it, you need to know that the secret pass phrase is
"speechiscode". Under what circumstances would the encrypted file be legal to publish?
(Contributed by Scott A. Crosby.) | |
| Bar codes |  Here
is a bar code version of the
anonymous C source code, contributed by Scott C. Potter. He writes:
"I used a :cue:cat model 68-1965 and a web based
decoder for testing." The cue:cat has generated its own
DMCA-related legal battles. Here
is a bar code version of the
anonymous C source code, contributed by Scott C. Potter. He writes:
"I used a :cue:cat model 68-1965 and a web based
decoder for testing." The cue:cat has generated its own
DMCA-related legal battles. | |
| Zebra label Barblocks |
 Zebra label barblocks, contributed by Lion J Templin. Type PDF417
barblocks, coded in ZPL for a Zebra commercial label printer, can hold
just over 1024 bytes. Three labels slapped on an envelope can send
DeCSS around the world. For the full story on this encoding, see
Lion's barblock
page. Zebra label barblocks, contributed by Lion J Templin. Type PDF417
barblocks, coded in ZPL for a Zebra commercial label printer, can hold
just over 1024 bytes. Three labels slapped on an envelope can send
DeCSS around the world. For the full story on this encoding, see
Lion's barblock
page. | |
| PNG palette encoding |
||
| 8-bit paper tape |
||
| Commodore 64 audio tape |