Adversary
Attacks
Quite frankly, a
lot of things can go wrong. Roughly there are three types of attacks that an
adversary can mount against a user. In increasing order of danger they are:
online attacks, offline attacks and phishing attacks. In an
online attack an adversary attempts to login as a legitimate user. Most
sites have a three strikes policy and will lock the adversary out after a few
incorrect guesses. Adversaries typically guess a popular
passwords (e.g., 123456, password, letmein).
Sadly many people are vulnerable to even this simple attack. In
the example below the adversary attempts to guess a user’s hotmail password.
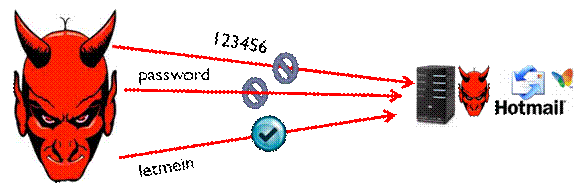
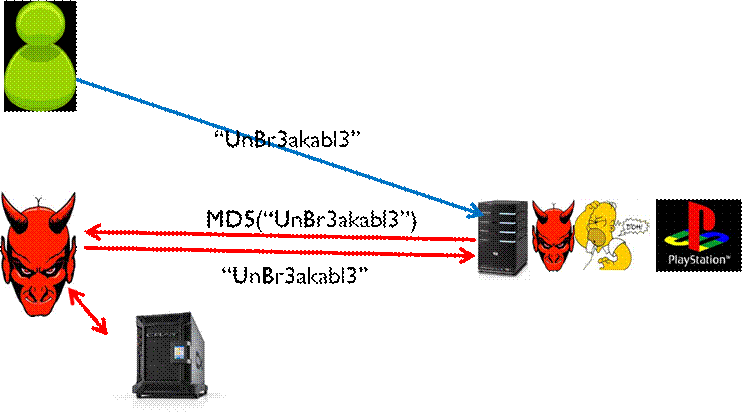
A second – more dangerous
attack – is an offline dictionary attack. In an offline attack the adversary
manages to obtain the cryptographic hashes of the user’s password (e.g., by
exploiting server vulnerabilities). Unfortunately, this scenario is quite
common (e.g., Sony,
Gawker,
LinkedIn,
Zappos). Once the adversary has access to the user’s
password hash he can run a password cracker to try to crack the user’s
password. The adversary is no longer limited by a three strikes rule. However,
the adversary is limited by time and money.
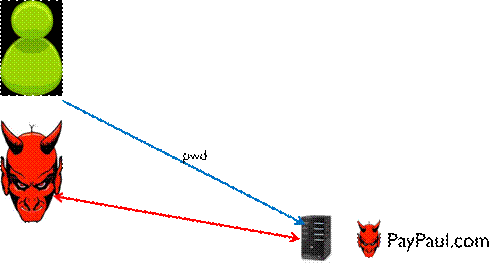
In the third
type of attack the adversary is simply able to obtain the user’s password
directly. In a phishing attack the adversary tricks the user into giving away
sensitive information (e.g., password, credit card number).
There are
several other ways that the adversary might directly obtain the user’s
password. If the user’s computer is infected with malware (e.g., a keylogger) when the user logs on to an account then an
adversary will be able to easily recreate the user’s password. While user
education could mitigate the effects of phishing attacks (e.g., check for
suspicious looking URLs) and malware (e.g., keep virus protection up to date,
update software regularly) an educated user may still be vulnerable (e.g. A
company like RockYou might store their passwords in the clear).
Once an
adversary obtains one of the user’s passwords he can use this information to
help guess the user’s other
passwords. The large datasets of cracked passwords has also helped hackers
to improve their password cracking attacks by revealing how users tend to pick
passwords.


